Google Chrome is often labeled as one of the best web browsers around for all the right reasons. Players like Firefox are competing by adding innovative features, but Chrome continues to enjoy an unparalleled popularity. However, this doesn’t mean that Chrome is 100% secure. A security researcher has spotted malicious add-ons that’s almost impossible to delete.
These extensions have been spotted in both Mozilla Firefox and Google Chrome. They use techniques to redirect users away from pages where they can remove the extensions and try to hijack traffic for driving clicks on other web pages.
Chrome and Firefox both are affected
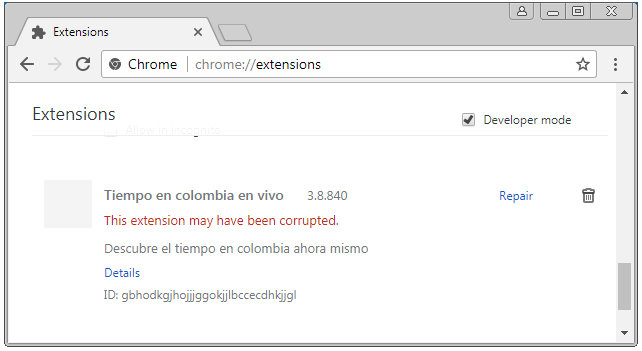
For Chrome, the researcher found an extension named Tiempo en colombia en vivo. It gets pushed via a method called “Forced Chrome Extension.”To drive away users from the extensions page, it redirects the uses from chrome://extensions/ to chrome://apps/?r=extensions. On this page, only installed apps are listed. Blocking JS in Chrome or starting Chrome with disabled extensions doesn’t help as well.
A method to stop the extensions from operating is by renaming the 1499654451774.js file in the extensions folder. It shows up in the extensions list as corrupted.
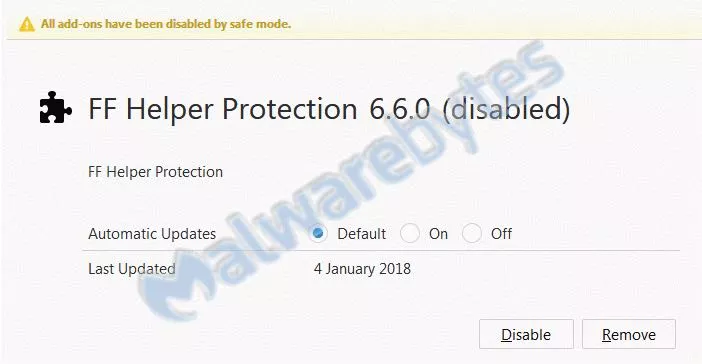
Malwarebytes also found a similar extension in Firefox with name PUP.Optional.FFHelperProtection. It blocks about:addons in background.js and prohibits the user from removing it.
Removal in Firefox is comparatively easier as one can see all the installed extensions by running the browser in safe mode.
While the exact extensions might not exist on the online stores at the moment, their modified versions continue to prevail. As they arrive on the machines of users via forced installs, it’s difficult to avoid them every single time. So, the users are advised to surf the web with caution and use recommended security methods. Before downloading extensions, users should also read their descriptions and reviews carefully.
It’s also worth noting that these extensions highlight a picture that involves Google’s failure to ensure proper scrutiny when it comes to Play Store or Chrome Store. So, unless Google makes its review process for third-party extensions and apps more stringent, such problems aren’t going to go away.